Time server MCSE with a BSc degree in engineering. Returning to work after a career break and studying like mad to update my certifications.
Monday 5 August 2013
Reset Windows 7 or Windows 8 Password
As always some of the best tips are found when you are looking for something else entirely. Here are a couple of nice tips for resetting local account password on Windows 7 & 8 - so simple and so insecure.
Booting the machine to a USB drive, DVD or slave the hard drive of another machine - rename some files and your in.
Reset a Windows 8 Password without using any third party software
Reset a Windows 7 Password without using any third party software
An alternative I have seen is to replace the sticky keys file with the cmd.exe. Sticky keys is activated at the logon screen if you press shift five times – but instead you bring up a command prompt.
Friday 19 July 2013
Windows 8.1 Preview
Windows Blue AKA Windows 8.1 Preview is here with a long list of changes. To see the long list of what’s new see the link below.
To download the preview here’s the link
Thursday 18 July 2013
Active Directory Recycle Bin Step-by-Step Guide
Active Directory Recycle Bin helps minimize directory service downtime by enhancing your ability to preserve and restore accidentally deleted Active Directory objects without restoring Active Directory data from backups, restarting Active Directory Domain Services (AD DS), or rebooting domain controllers.
When you enable Active Directory Recycle Bin, all link-valued and non-link-valued attributes of the deleted Active Directory objects are preserved and the objects are restored in their entirety to the same consistent logical state that they were in immediately before deletion. For example, restored user accounts automatically regain all group memberships and corresponding access rights that they had immediately before deletion, within and across domains.
Active Directory Recycle Bin is functional for both AD DS and Active Directory Lightweight Directory Services (AD LDS) environments.
Extract for TechNet for full article see link below
Deploying a GlobalNames Zone (GNZ)
A common requirement in computer networks is the ability to resolve simple, single-label names. The use of single-label names makes it possible for a computer to access hosts such as file and Web servers by using short, easy-to-remember names instead of the fully qualified domain names (FQDNs) that form the default naming convention for Domain Name System (DNS). To make the use of single-label names possible, many networks deploy Windows Internet Name Service (WINS) technology and servers in their environment. As a name resolution protocol, WINS is an alternative to DNS. It is an older service that uses NetBIOS over TCP/IP (NetBT). WINS and NetBT do not support Internet Protocol version 6 (IPv6) protocols; therefore, they are being phased out in many networks.
To help network administrators migrate to DNS for all name resolution, the DNS Server role in Windows Server 2008 supports a specially named zone, called GlobalNames. By deploying a zone with this name, you can have the static, global records with single-label names, without relying on WINS. These single-label names typically refer to records for important, well-known and widely-used servers—servers that are already assigned static IP addresses and that are currently managed by IT-administrators using WINS.
The GlobalNames zone is not designed to be a complete replacement for WINS. You should not use the GlobalNames zone to support the name resolution of records that are dynamically registered in WINS, records which typically are not managed by IT administrators. Support for these dynamically registered records is not scalable, especially for larger customers with multiple domains or multiple forests.
This is an extract from a TechNet article see the link below for the full article.
TechNet: Deploying a GlobalNames Zone
Additional references
Wednesday 17 July 2013
Securing Accounts After an RODC Is Stolen
Having work for large organisations with many branch offices it was not an infrequent event to have equipment stolen.
From experience … the people that stole your kit know you will be sending out new kit so they will return for that.
Read Only Domain Controllers (RODC) are designed for insecure environments .. so what do you do if one gets nicked … you follow the procedure on the link below to disable the stolen RODC and reset the passwords on any cached user accounts.
Tuesday 16 July 2013
Managing AD LDS using PowerShell
Microsoft Active Directory Lightweight Directory Services (AD LDS) is an independent mode of Active Directory that provides dedicated directory services for applications.
MSDN: Active Directory Lightweight Directory Services
AD LDS can use many of the familiar tools used to manage Active Directory Directory Services (AD DS) even when it comes to using the AD PowerShell Module there is a feeling of “deja vu”.
On the link below you will find a list of Active Directory cmdlets that can be used to manage AD LDS instances.
Windows 2008 R2: Managing AD LDS using the AD PowerShell Module
Sunday 7 July 2013
Command-line switches for Outlook 2010
You can change Outlook 2010 by adding switches to the outlook.exe command.
For example
outlook.exe /resetfolders
Restores missing folders at the default delivery location.
For a full list of switches see the following link.
Saturday 6 July 2013
Multiple mailboxes open in OWA 2010
One of the first things I found with Outlook Web Access 2010 is that you cannot have multiple mailboxes open in separate tabs; you get the following error message.
You can resort to a second browser like Chrome or Firefox to get a second mailbox open. I have tried a second tab in Chrome and get the same result …one mailbox per browser.
The solution
Create a shortcut on your desktop remembering to add <your_servername> without <>.
"C:\Program Files\Internet Explorer\iexplore.exe" -noframemerging /owa">https://<your_servername>/owa
Click the shortcut every time you want an additional OWA session. You can now open multiple OWA mailboxes in separate instances of internet explorer.
Monday 1 July 2013
Ensuring that group policy is applied before logon
By default group policies are applied asynchronously - Fast Logon Optimization . The upshot is that if you update a policy users may logon before the latest policy is applied and it may take a couple of logons before current settings are applied.
I am messing about with GPOs in a test environment so I don’t want to have to constantly rebooting PC or perform multiple logons attempts.
Disable Fast Logon Optimization by using the following
Create or update and existing group policy attached to the OU housing the computers and edit the following.
Computer Configuration
Policies
Administrative Templates
System
Logon
Enable: Always wait for the network at computer startup and logon
Sunday 30 June 2013
Redirecting the users and computers containers
By default Active Directory places user accounts, computer accounts, and groups in CN=objectclass containers.
Redirecting the default container for user, computer, and security groups to an organizational unit permits Group policies to be applied.
Microsoft considers it "best practice" to place security principals into an organizational unit hierarchy that mirrors your organizational structure, geographic layout, or administration model.
Redirect Users
redirusr <DN path to alternate OU>
redirusr ou=myusers,DC=contoso,dc=com
Redirect Computers
redircmp <DN path to alternate OU>
redircmp ou=mycomputers,DC=contoso,dc=com
Redirecting the users and computers containers in Active Directory domains
Considerations
Windows Server 2003 domain functional level or higher required.
The default User and Computer containers are protected against accidental deletion remember to ensure that you do the same with your new OUs.
Friday 28 June 2013
User Template increase attributes copied
When you create a user template and copy it to create a new user only a limited number of attributes are copied
Example: Copy Office From the General tab
Suppose you have a user template and want the Office value from the general tab to remain when you create a new user by copying the template.
You can use ADSI Edit to make the attribute copy.
- Open ADSI Edit
- In the left pane right click ADSI Edit and Connect To the Schema Naming Context
- Locate the attribute name in this case Office is:
Physical-Delivery-Office-Name - Right Click and open Properties
- Attribute Editor Tab … locate searchFlags
- Edit and add 16 to the value
- To prevent it from copying remove 16 from the value.
I have tested with Windows 2008 R2 as shown but certain it should work with previous version as I learned from a Windows 2000 KB Article.
Where do you get the attribute names … I found some here.
Tuesday 25 June 2013
Ultrasound - File Replication Service
Ultrasound - Monitoring and Troubleshooting Tool for File Replication Service (FRS)
Ultrasound is a monitoring and troubleshooting tool for the File Replication Service (FRS). FRS is a legacy technology that replicates files and folders that are stored in Distributed File System (DFS) folders or in the System Volume (SYSVOL) folder on domain controllers.
Sunday 23 June 2013
Learn Windows PowerShell in a Month of Lunches
Here are some companion videos to an excellent PowerShell book.
Friday 21 June 2013
Active Directory Shadow Groups
Simply: You have an OU in active directory … add any user accounts in the OU to a group … in addition you want to maintain the membership when accounts are added or removed from the OU.
The following link includes examples using the ds* commands and PowerShell to populate and maintain Shadow Groups.
Shadow Groups in Active Directory
It should be possible to expand these examples to include the user accounts from other OUs or to use Identity Attributes rather than OU.
Tuesday 18 June 2013
Cmdlet Reference for Windows Server 2008 R2
Powershell Cmdlet help for Windows Server® 2008 R2 roles and features
Thursday 13 June 2013
Windows Server 2012 Upgrade Jump Start (70-417)
This is session one of a twelve, a good start point for 70-417
Tuesday 11 June 2013
PowerShell determine what version is installed
What version of PowerShell is installed on a machine
Open PowerShell and type Get-Host
Windows 7 – version 2.0
Windows 8 – version 3.0
Sunday 9 June 2013
Update GPO templates to manage Windows 8
You’ve added some Window 8 PCs and possibly Windows Server 2012 to your existing Windows Server 2008 R2 enterprise … okay so how do you access the additional features with Group Policy?
Looking at a Group Policy setting in Windows 8 Windows 8 GPO Blocking Connection Accounts … I got to thinking … I’m doing this from Windows Server 2012 … more realistically I will be adding Windows 8 machines to a Windows Server 2008 environment.
How do I update the group policy template files?
My only caveat … I have still to do the testing … will the new templates work with the old admin tools.
Windows 7, Windows Server 2008 R2 Group Policy Central Store
Administrative Template files for Windows 8 & Windows Server 2012
Upgrading the ADMX Central Store files from Windows 7/2008R2 to Windows 8/2012
Windows 8 GPO Blocking Connection Accounts
In Windows 8 you can associate your domain user account with your Microsoft Live ID. Not something that the enterprise would necessary welcome ... so how do you disable it.
Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options\Accounts:Block Microsoft Accounts
If you disable or do not configure this policy, users will be able to use Microsoft accounts.
If you select the "Users can’t add Microsoft accounts" option, users will not be able to create new Microsoft accounts on this computer, switch a local account to a Microsoft account, or connect a domain account to a Microsoft account. This is Microsoft's preferred option if you need to limit the use of Microsoft accounts in your enterprise.
If you select the "Users can’t add or log on with Microsoft accounts" option, existing Microsoft account users will not be able to log on to Windows. Selecting this option might make it impossible for an existing administrator on this computer to log on and manage the system.
I would expect the latter option to be the case in a Windows 2008/ Windows Server 2012 enterprise.
Saturday 8 June 2013
Enable GodMode in Windows 7 and Windows 8
Want all your admin features in one place. Really useful if you are transitioning from Windows 7 to Windows 8. Think it has been around since Windows Vista.
Create a folder on your desktop and rename it
GodMode.{ED7BA470-8E54-465E-825C-99712043E01C}
Your folder will be remained GodMode and inside will be all the good stuff an Admin God would want.
GodMode folder Windows 7
GodMode folder Windows 8
Windows 8 elevated command prompt
Working with Windows 7 I found the quick way to an elevated administrators command prompt was Windows key + R to open the Run box, type cmd then press Ctrl+Shift+Enter. In fact I used this method for most thing I wanted to run as administrator.
This method does NOT appear to work with Window 8 … this is where the Windows 8 haters start to scream … but the solution is as simple.
There are several ways to elevated command prompt in Windows 8 my preferred method from the Desktop is:
Press the Windows key to return to the start screen.
Type cmd
Command Prompt will return already selected
You now press Ctrl+Shift+Enter
Say yes to the UAC prompt
You are returned to the desktop with an elevated command prompt in no more time than it took in Windows 7.
It would be nice for the transition from 7 to 8 if Windows Key + R then Ctrl+Shift+Enter worked or did I miss the memo and it should!!!
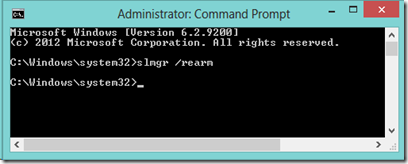
Extending - rearming Windows 8 Evaluation
To extend the grace period of your Windows 8 evaluation open an elevated command prompt and enter
slmgr /rearm
This extends your evaluation for a further 30 days.
Can be rearmed 3 times in theory extending your trial by 90 days.
Enable/Disable Store in Windows 8 Group Policy
Quick Guide
Local Group Policy Editor (run gpedit.msc)
User Configuration\Administrative Templates\Windows Components
Store
Turn off the Store application
In Detail
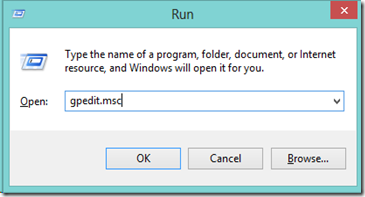
Press Windows Key + R to open the Run box
enter gpedit.msc (don’t forget the file extension)
This will open the Local Group Policy Editor
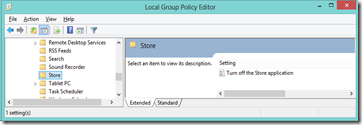
In the left pane under user configuration expand Administrative Templates then Windows Components
Still in the left pane under Windows Components Select Store
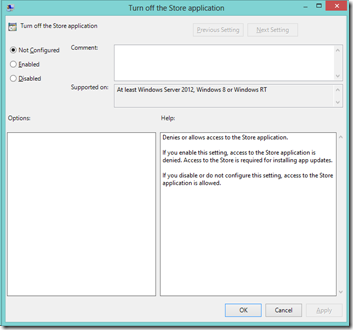
In the right pane open (double click) Turn of the Store application
By default is the Store is enabled
To disable the store you must Enable this policy option
Select the enable radio button and press OK
To enable the store select Disabled or Not Configured
There is no to save option just close the group policy editor
Tuesday 4 June 2013
Windows 7 Network Tracing
Tools for Troubleshooting using Network Tracing in Windows 7
MSDN: Using Netsh to Manage Traces
Thursday 30 May 2013
Certificate Services Installing CA
The preferred method
Microsoft best practice is to install a standalone root CA with an enterprise subordinate CA. The Standalone can then be isolated offline for enhanced security while the subordinate takes over issuing certificates.
The following videos gives a short demo of installing two CAs using server 2003 … it is a good starting point for his 2008 videos.
Microsoft CA 1 of 2 - Setup Standalone Root
Microsoft CA 2 of 2 - Enterprise Subordinate
The following video gives a short demo of CA autoenrollment using server 2003.
Microsoft CA - Autoenrollment Step-by-Step
In reality a single tier
While it is best practice to have two CAs … see above … in many instances you may only have one server at your disposal.
Single Tier PKI one CA that does all the issuing of certificates aimed at small business of up to 300.
Certificate Services 2008 R2 - Installing a Single Tier PKI
SSL in depth
Certificate Services 2008 1 of 4 - Installing a Microsoft CA
Certificate Services 2008 2 of 4 - Implementing a SSL Certificate
Certificate Services 2008 3 of 4 - Binding the SSL Certificate
Certificate Services 2008 4 of 4 - SSL Under the hood
Certificate Services 2008 1 of 2 - Autoenrollment (concept)
Certificate Services 2008 2 of 2 - Autoenrollment Step By Step
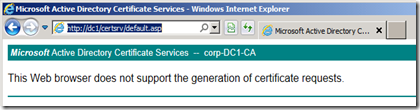
Windows CA 2008 and IE10 Error
When messing around with Certificate Services on Windows Server 2008 R2 and trying to connect to the CA’s certsrv folder in the browser I got the error:
“The Web Browser does not support the generation of certificate requests”
The problem is related to IE 10; if I switch to compatibility mode no problem.
News and information for public key infrastructure (PKI) and Active Directory Certificate Services (AD CS) professionals.
Hyper-V VMs continually shutting down
I have an issue with my Virtual Machines (VMs) shutting down after a short period. It would appear to be related to the operating system expiring.
Happens with Windows Server 2008 VMs … Windows 7 VMs appears to be okay.
One solutions is rearming from the command prompt with
slmgr.vbs –rearm
The post I got the fix from mentioned that this would reoccur in about 5 days.
I suspect that the VMs will have to be rearmed every time they are reverted. A small annoyance in a test environment but in a production environment … where is your licence!!
Monday 20 May 2013
Using Certificates for IPsec Authentication
In a previous post IPsec Overview there is an example of securing Telnet with IPsec. This link to a TechNet Video takes the Telnet example further by using Certificates for IPsec Authentication.
IPsec Overview
Useful overview of IPsec with example of setup using group policy.
I have included a link to the contributors YouTube site
Sunday 19 May 2013
Basics of IPv6 for Vulcans
Found this useful to understand the basics of IPv6 even if the guy looks like a Vulcan. Busy watching the other two parts.
Thursday 16 May 2013
Useful NetSH IPv6 commands
Here is a link to some useful commands for working with IPv6 from the command line using NetSH.
Useful Windows 7 IPv6 netsh commands
One I would add is to include a rule in Windows 7 Firewall to reply to ping requests ... useful when testing as Windows 7 does not reply to ping by default.
netsh advfirewall firewall add rule name="All ICMP V6" protocol=icmpv6:any,any dir=in action=allow
I was working on a Microsoft IPv6 lab and they would have appeared to have omitted this step before requesting you to ping the client.
Wednesday 15 May 2013
Messing about with NetSH AdvFirewall
Reset Firewall to Default
If you are going to mess about with your firewall the first thing you want to know is how to reset it to default
netsh advfirewall reset
Export/Import Settings
The second thing you should know is probably the last thing you would have though about. If you are going to mess around with an already successfully configured firewall then you may want to save the current settings and reimport them.
netsh advfirewall export "c:\wfconfig.wfw"
netsh advfirewall import "c:\wfconfig.wfw"
It’s not a bad idea if you are messing about with NetSH in general to export the configuration. Not all “learning” is done with easily revertible test VMs … most of the important lesson we learn tend to be on live systems.
Firewall Off & On Test
If I switch the firewall off will this work … NO … better switch it back on then.
netsh advfirewall set allprofiles state off
netsh advfirewall set allprofiles state on
Useful WMIC Queries
WMI using the command line, WMIC is a utility that allows you to interact with WMI from a WMI-aware command-line shell.
Here are a couple of useful links
Tuesday 14 May 2013
Microsoft Windows DNSLint utility
DNSLint is a Microsoft Windows utility that helps you to diagnose common DNS name resolution issues.
DNSLint has three functions that verify Domain Name System (DNS) records and generate an HTML report. The three functions are:
- dnslint /d: This diagnoses potential causes of "lame delegation" and other related DNS problems.
- dnslint /ql: This verifies a user-defined set of DNS records on multiple DNS servers.
- dnslint /ad: This verifies DNS records specifically used for Active Directory replication.
Sunday 12 May 2013
Windows 8 PowerShell Shutdown Tile
TechNet link to a PowerShell module to create Shutdown, Restart and Logoff tiles for your Windows 8 Start screen.
Create a Shutdown/Restart/Logoff Windows 8 Tile for the Start menu (PowerShell)
Windows 8 Desktop Shutdown Shortcut
I don’t share a lot of peoples dislike of Windows 8 … want to shutdown … then create a Shutdown shortcut on the desktop
shutdown /s /t 0
That would be Zero not and Oh!!!
Windows 8 Classic Shell, Shutdown & Annoyances
While I don’t share a lot of peoples immediate hatred of Windows 8, having been through a few new versions of Windows, there are a few annoyances.
Do you want the start button download this.
The other immediate annoyance I had was Metro Applications taking up the whole screen switch to Google Chrome.
If you don’t like a Metro App hogging the whole screen change the file association to a third party app.
Thursday 9 May 2013
Windows Server 2012 Local Users and Groups
If you are from a Windows Server 2008 background you are may be looking for access to Local Users and Groups in Windows Server 2012.
On the Start screen type Computer
Select Computer Manager
You will find yourself back in familiar territory.
Hyper-V Using Differencing Disks
One way to optimize disk space and reduce the number of times that you have to install and update a released operating system is to create parent child configurations using differencing disks in Hyper-V.
For example, if you need to install a test lab that will employ three Windows Server 2008 R2 installations: one configured as a domain controller, another configured as an Exchange Server, and a third configured as a SQL Server, you could use a Parent-Child Differencing disk configuration to save the time of installing and updating the Windows Server 2008 R2 installation for all three of those virtual machines.
TechNet: Hyper-V Virtual Machine (VM) Parent-Child Configuration Using Differencing Disks
Monday 6 May 2013
Windows Denial of Service by IPv6 RA Packets
Any version of Windows with IPv6 installed and running is vulnerable to a DoS attack by sending thousands of Router Assignment (RA) packets.
To prevent a “Script Kiddies” attack have a look at this link.
Overclocked Techies: Windows Denial of Service by IPv6 RA Packets
Sunday 5 May 2013
Microsoft Evaluation VHD Administrator Password
Recently decided to use the evaluation VHD of 2008 R2 I downloaded from Microsoft .. but what was the password.
Goggled the file name …
“windows server 2008 r2 enterprise evaluation (full edition)”
… and found the password was Pass@word1.
It was then I remembered the problems I had with that password in the past.
The VM was created using the US local & keyboard settings if you are using a UK keyboard you have to type
Pass”word1
Saturday 4 May 2013
Manage Hyper-V 2012 on Core from Windows 8
Unlike Window 7 and Hyper-V on 2008 R2 there is no need to download additional tools to administer Hyper-V from Windows 8 as they are a feature of Windows 8.
This is the Client Side Configuration there are plenty of postings relating to server side configuration. Both machines are in same workgroup.
Install Hyper-V Management Tools on Windows 8
Search for Control Panel
Select Control Panel then Programs
Under Programs and Features Heading select Turn Windows Feature On or Off
Tick Hyper-V Management Tools and both sub options
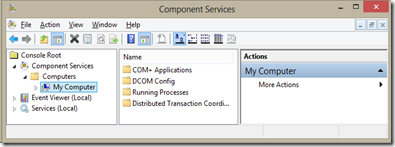
Start Component Services
Search "DCOMCNFG"
right click and "Run as administrator"
Select Console Root, Component Services, Computers, My Computer
Right click My Computer and select properties
Select "COM Security"
Select "Edit Limits" for Access Permissions

Allow remote access by setting the checkmark for the "ANONYMOUS LOGON"
Windows 2012 Local Users and Groups
Another how do I find it with Windows 2012; Local Users and Groups.
search for lusrmgr.msc
Windows 2012 Core Disk Performance Missing
If you open Task Manager and go to the Performance tab Disk performance is missing.
Did a quick web search and someone remembered with NT 4.0 you had to enable this with …
diskperf –y
… and it works with Windows Server 2012 Core.
That takes me back.
Friday 3 May 2013
TechNet: Test Lab Guides
Test Lab Guides (TLGs) allow you to get valuable hands-on experience with new products and technologies using a pre-defined and tested methodology that results in a working configuration. When you use a TLG to create a test lab, instructions define what servers to create, how to configure the operating systems and system services, and how to install and configure any additional products or technologies.
A challenge in creating useful TLGs is to enable their reusability and extensibility. Because creating a test lab can represent a significant investment of time and resources, your ability to reuse and extend the work required to create test labs is important.
Thursday 2 May 2013
DirectAccess Deployment Guide
This link describes deployment of DirectAccess in Windows Server 2008 R2.
Discusses such things as Corporate Connectivity Detection.
Sunday 28 April 2013
Microsoft Application Compatibility Toolkit 5.6
The Microsoft Application Compatibility Toolkit (ACT) version 5.6 contains the necessary tools and documentation to evaluate and mitigate application compatibility issues before deploying Windows 7®, Windows Vista®, a Windows Update, or a new version of Windows Internet Explorer® in your environment.
What caught my eye. If you enable compatibility logging for Internet Explorer if ACT is not installed then some event ids in Event Viewer lack descriptions. I installed it to add functionality to Event Viewer
Friday 26 April 2013
Check firewall not blocking shared printing
Couple of quick ways to check if the firewall is blocking a shared printer.
From a remote machine open an command prompt and use
Net View \\print-server-name
This should return a list that includes the name of the shared printer generally you can now eliminate the network or firewall as an issue.
or download PortQry from Microsoft and check the required ports are open on the computer sharing the printer.
Use PortQry or PortQueryUI to check TCP ports 445 & 139
If computers are not on the same LAN segment don’t just check the print server firewall ensure their is not another firewall between the computers.
Thursday 25 April 2013
Remote Desktop printing add additional drivers
I run Hyper-V with a mix of 32bit/64bit operating systems and would like to print from any of the remote session to my local printer.
My ancient HP LaserJet 1200 has the default Windows 7 32bit driver installed but I cannot get the additional 64bit driver to install.
I seem to remember a similar situations in the past with a network printer where the resolution was the printer had a different name in the 32 bit inf than the 64 bit. I hacked the 64 bit inf file and ensured the names matched exactly … with success.
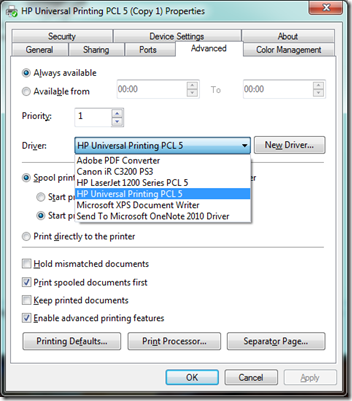
Did not want to go through that again and thought that I would try the HP Universal Printing PCL 5 drivers installed from the command line with PNPUTIL.EXE … why … never used it and wanted to try it.
- Downloaded both versions of the driver from HP
- Installed the 32 bit driver from an elevated command prompt
- pnputil –a c:\<path>\*.inf
- and did the same with the 64 bit
- opened the printer properties, advanced tab and switched the driver to the HP Universal Printer PCL5
As I did not intend blogging this I forget whether I had to go to the share tab and add the additional drivers or whether it was smart enough to find it for itself.
Painless and I can now print from 64bit VMs
Print spooler must be running on server and client
Read something like this … “In order to print to a server based printer the print spooler must also be running on the client” … time to experiment … It is the same with a Remote Desktop session and a locally attached printer?
Did an experiment, I used Remote Desktop from a Window 7 machine to a Windows 7 VM. Remote Desktop is setup allow the remote session to use the local printer.
Succeeded in printing from notepad on the remote machine to the redirected LaserJet on my local machine.
Shut down the spooler on the remote session with
net stop spooler
and tried to print from notepad got this error and
everything disappeared the from Select Printer except Add Printer
restarted using net start spooler
all the printer came back.
Remote/Shared printing … the spooler must be running on both machines not just the box the printer is plugged into.
Monday 22 April 2013
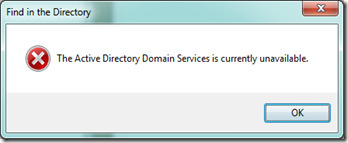
Search Active Directory from the Desktop
To quickly get the AD search box up on a domain joined PC create a shortcut on the desktop with item location set to.
%SystemRoot%\SYSTEM32\rundll32.exe dsquery,OpenQueryWindow
Domain joined PC only, try to do it from a workgroup you will get:
Sunday 21 April 2013
Server 2008 R2 core remotely edit group policy.
Windows Server 2008 R2 Core remotely edit group policy.
I have a Windows 7 computer that I use to manage Hyper-V on Windows 2008 R2 core. Both machine are in the same workgroup.
On Windows 7
Start, In Search Programs and Files enter MMC
When the Microsoft Management Console starts open File, Add/Remove Snap-in…
Select “Group Policy Object Editor” click Add > button.
Click Browse button
Select Another computer and type the name or IP of remote machine
Click OK then Finish and you should now be able to View\Edit the Local Group Policy on the remote server
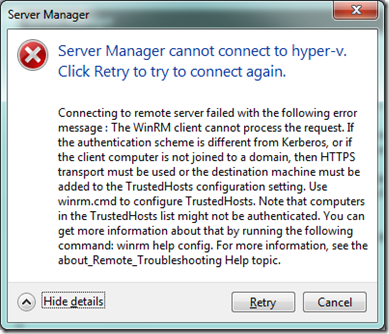
Remote Server Manager on Server 2008 R2 Core
I have a long standing Hyper-V test environment running on Server 2008 R2 core. Recently decided to try Server Manager remotely from a Windows 7 machine to manage the 2008 Core.
Both machines are in the same workgroup and successfully configured for Remote Desktop. The Remote Server Administration Tool for Windows 7 are installed.
Run Server Manager on Windows 7 then try connecting to Hyper-V server and I get this error:
TechNet: Remote Management with Server Manager
On Hyper-V Server
Ensured that I had done the following
- From sconfig.cmd
- selected 4) Configures Remote Management the server
- then 3) Allow Server Manager Remote Management
this had no effect on the error there was no need to reboot the server as I had already installed PowerShell but did so anyway but still could not connect with Server Manager
On Windows 7 Client
net start winrm
winrm set winrm/config/client @{TrustedHosts="RemoteComputerName"}
Replace RemoteComputerName with server name
This failed on initial attempt
I should have run the following command first because machines where in workgroup not domain.
reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v LocalAccountTokenFilterPolicy /t REG_DWORD /d 1 /f
Running the winrm command again and Server Manger could connect to my Hyper-V server.
Still got errors on Server Manager components but a step forward.
Device Manager Error
Resolution Enable Remote Access to Device Manager
See this very useful blog post
Enabling Remote Access to Device Manager on Server Core
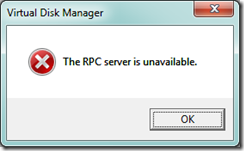
Virtual Disk Management Error
Resolution Windows 7 Firewall
Inbound rules on Windows 7 needed to be set
Remote Volume Management - Virtual Disk Service (RPC)
Remote Volume Management - Virtual Disk Service Loader (RPC)
Saturday 20 April 2013
Migrating Hyper-V 2008 R2 Core to 2012 Core
I may be wrong … but on first evaluation it appears you cannot transfer Virtual Machines with Snapshots.
It would also appear that an in-place upgrade from Hyper-V 2008 running on core to Hyper-V 2012 running on 2012 core is not on.
Looks like my upgrade to Hyper-V 2012 will have to be put on hold.
Here is a Microsoft TechNet Blog explaining how to migrate from Hyper-V 2008 to Hyper-V 2012 on the core.
Step-by-Step: Migrating to FREE Microsoft Hyper-V 2012 Servers AND Clusters from 2008 R2 and VMware
Monday 15 April 2013
Hyper-V 2008 Core Memory Requirements
Sunday 14 April 2013
Small Business Server 2011 with only 4GB RAM
If you follow minimum requirements you would allocate 8GB ram for a virtual machine just to evaluate Small Business Server 2011.
Although the motherboard on my Hyper-V system should take this in it stride the jump from its current 8GB to its 16GB max is expensive.
So do I need 8GB to evaluate SBS 2011? I couldn’t if I wanted to as Hyper-V needs some RAM so I gave it 6GB and it fired up. What about 4GB SBS 2008 worked on this and the only reason 2011 wants 8GB is Exchange 2010.
Here is a shot of my task manager running with 4GB of memory and the Exchange Console running. Onwards with the evaluation.
I have also stopped WSUS from downloading but not disabled it.
Disable WSUS on Small Business Server
I have various versions of Small Business Server running in an evaluation environment and don’t want WSUS constantly downloading updates here is a useful guide from the SBS Diva Blog. Should work for SBS 2008 and 2011.
The guide demonstrates how to prevent WSUS downloading updates without mangling the system. You in effect just put WSUS into a monitoring state.
Rearm Windows 2011 SBS Evaluation
Something always comes up when you are trying to evaluate a product and X weeks/months later you fire up the virtual machine and the Grace Period has expired.
slmgr.vbs –dli will tell you how long the grace period is.
slmgr.vbs –rearm will reset it.
I have tried this on a couple of product the latest being an evaluation version of Small Business Server 2011 and the grace period was reset to 30 days.
If memory serves me then it should work for Windows 2008 evaluations.
Don’t know if it works with products like Windows 8 or Server 2012.
Performance Tuning for Windows Server 2008
Came across this guide while looking for something else may be of use if I ever get time to read it.
This guide describes important tuning parameters and settings that can result in improved performance for the Windows Server 2008 operating system. Each setting and its potential effect are described to help you make an informed judgment about its relevance to your system, workload, and performance goals.
Saturday 13 April 2013
Windows 7 RTM … No more support
As of April 9th 2013 you cannot get mainstream support from Microsoft for Windows 7 without a service pack.
Mainstream Support stops for Windows 7 13th January 2015
Windows 7 in it virgin form is no longer supported you have to add at least service pack 1.
When does Windows SP1 support end?
Looks like SP1 support will end 13th January 2015
SP1 support stops 24 months after the release of SP2 or when mainstream support stops on 13th January 2015 which ever comes first.
See the following Springboard Series Blog
Windows Firewall Learning Roadmap
If you are new to Windows Firewall with Advanced Security, this topic can help you identify what you need to learn to fully understand and use all of the features available in Windows Firewall with Advanced Security.
It includes prerequisite topics that cover a variety of networking fundamentals.
TechNet: Windows Firewall with Advanced Security Learning Roadmap
Thursday 11 April 2013
Lost Your Microsoft Licence Key
Where is the product key … in what file … in what filing cabinet. If you’ve worked in technical support for any length of time you know product keys are more likely to be found down the back of a filing cabinet than in it … or were thrown out with the packaging.
Here is a tool from the CNET web site that gives you the keys of the Microsoft products installed on your machine … could not be bothered getting out of my seat to hunt for my Office licence key!!!
Saturday 6 April 2013
Windows 7 Firewall Documentation
Windows 7 Firewall Documentation
Here are some useful TechNet links covering the subject:
TechNet: Windows Firewall with Advanced Security and IPsec
TechNet: Networking and Access Technologies - Windows Firewall
Windows Firewall with Advanced Security Getting Started Guide
Netsh Commands for Windows Firewall with Advanced Security
From TechNet Networking Blog
Thursday 4 April 2013
User State Migration Tool 4.0 User's Guide
Windows® User State Migration Tool (USMT) 4.0 is a scriptable command-line tool that provides a highly-customizable user-profile migration experience for IT professionals.
USMT includes two components, ScanState and LoadState, and a set of modifiable .xml files: MigApp.xml, MigUser.xml, and MigDocs.xml. In addition, you can create custom .xml files to support your migration needs. You can also create a Config.xml file to specify files or settings to exclude from the migration.
TechNet User State Migration Tool 4.0 User's Guide
USMT used in the migration to Windows 7 note the following:
You can migrate a 32-bit operating system to a 64-bit operating system. However, you cannot migrate a 64-bit operating system to a 32-bit operating system.
USMT 4.0 does not support any of the Windows Server® operating systems, Windows 2000, or any of the starter editions for Windows XP, Windows Vista, or Windows 7. In addition, USMT 4.0 only supports migration from Windows XP with Service Pack 2 or Service Pack 3.
BranchCache Early Adopter’s Guide
Looking for some study materials on BrancheCache as it relates Windows 7 and Windows Server 2008 R2.
Wednesday 3 April 2013
Windows 7 DiskPart & Virtual Hard Disks (VHD)
DiskPart.exe and managing Virtual Hard Disks (VHDs) in Windows 7
A useful MSDN blog posting about creating and attaching VHDs in Windows 7
Used DISKPART to create a VHD on my Windows 7 laptop dumped some files in it then moved it to my Hyper-V server and attached it to a Windows 7 Ultimate VM. Just a thing to know.
DiskPart.exe and managing Virtual Hard Disks (VHDs) in Windows 7
Monday 1 April 2013
Microsoft Baseline Security Analyzer 2.2
The Microsoft Baseline Security Analyzer provides a streamlined method to identify missing security updates and common security misconfigurations. MBSA 2.2 is a minor upgrade to correct minor issues and add optional catalog support.
MBSA 2.2 runs on Windows Server 2008 R2, Windows 7, Windows Server 2008, Windows Vista, Windows Server 2003, Windows XP and Windows 2000 systems and will scan for missing security updates, rollups and service packs using Microsoft Update technologies. MBSA will also scan for common security misconfigurations (also called Vulnerability Assessment checks) using a known list of less secure settings and configurations for all versions of Windows, Internet Information Server (IIS) 5.0, 6.0 and 6.1, SQL Server 2000 and 2005, Internet Explorer (IE) 5.01 and later, and Office 2000, 2002 and 2003 only.
You can scan the local machine or a group of machines
Download the 32bit or 64bit version from the link below:
Microsoft Baseline Security Analyzer 2.2 (for IT Professionals)
Windows 2008 R2 rearm activation grace period
You know how it is new version of a Microsoft product appears and the old evaluation versions disappear. Windows 2008 Evaluation version get it before it’s gone.
How to manually rearm the 10 day activation grace period
When the initial 10-day activation period nears its end, you can run the Slmgr.vbs script to reset it back to 10 days. To do this, follow these steps:
This resets the activation period to 10 days, and can be used up to four times. After this you will need to either activate or reinstall the evaluation.
Get the Windows 2008 R2 evaluation download from here:
Network Access Protection (NAP)
Network Access Protection
Network Access Protection (NAP) is a feature in Windows Server 2008 that controls access to network resources based on a client computer’s identity and compliance with corporate governance policy. NAP allows network administrators to define granular levels of network access based on who a client is, the groups to which the client belongs, and the degree to which that client is compliant with corporate governance policy. If a client is not compliant, NAP provides a mechanism to automatically bring the client back into compliance and then dynamically increase its level of network access.
In short is your OS AV up to date if not I am going to use WSUS and and the AV server to patch your system before I allow you to access the network.
Sunday 31 March 2013
Windows 7 BitLocker on Hyper-V Virtual Machine
A posting on a MSDN blog … Basically how to run BitLocker on a Windows 7 VM without access to the host’s TPM chip using a virtual floppy to hold the start-up key to allow the machine to boot.
Friday 29 March 2013
Windows 7 … I can remember the password now!!!
Password Recovery Disk
Did a little experiment with Windows 7 on a Hyper-V VM.
Created a fresh user account on a non-domain VM
Attached and formatted a Virtual Floppy.
Created a password recovery disk for this new user.
Got the password wrong and reset the password multiple times using the password reset disk.
Logged on as a local admin and reset the test account password. I expected this to make the password recovery disk useless … NO … could still use the password recovery disk to reset the password to get back into the user account.
Okay what about encrypted files?
Created a very important text document and encrypted it.
If you logon as local admin and change the password the user should NOT be able to get back into the file.
Logged on as the user with the changed password and could NOT access the encrypted file as expected.
What if … I can remember the password now!!
Used the password recovery disk to change the password back to the one used when the file was encrypted and I could get back into the encrypted file.
What if I change the password again using the Password Recovery Disk … YES … can still get into the encrypted file.
Useful tool or great big gapping security hole!!!
You decide …
Default Local Groups
Windows 2008 and Windows 7 Default Local Groups
Did you know:
- The Power Users group has no default rights, is present for backward compatibility and has no more rights than the Users group. A security template must be applied to enact its legacy role.
- Members of the Users group cannot share folders or create local printers.
While user rights can be configured through Group Policy it is still easier and more transparent to apply through security groups.
| Administrators | Unrestricted access |
| Backup Operators | Override file and folder access to backup and restore data. |
| Cryptographic Operators | Windows need to be deployed in Common Criteria Mode |
| Distributed COM Users | Manipulate Distributed COM objects |
| Event Log Readers | Read event logs |
| Network Configuration Operators | Change TCP/IP settings |
| Performance Log Users | Schedule logging of performance counters, enable and collect event traces |
| Performance Monitor Users | Access performance counter data locally and remotely |
| Power Users | Legacy use only |
| Remote Desktop Users | Use remote desktop |
| Replicator | Support file replication in domain |
For a fuller understanding of the Default Local Groups visit the TechNet link it is Windows Server 2008 but relates to Windows 7
Credentials Manager virtualapp/didlogical
On opening Windows 7 or Windows 8 Credentials Manager you may notice under Generic Credentials virtualapp/didlogical with a random username you do not recognise.
This appears to be a harmless entry for Windows Live. If in doubt delete but it may return uninstall Windows Live and it should stay away.
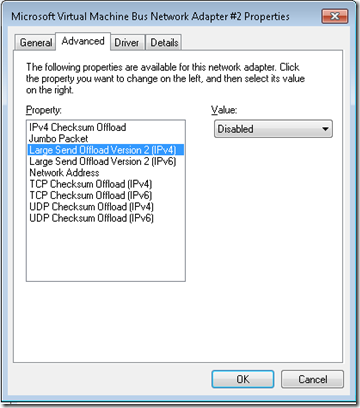
Hyper-V Remote Desktop Slow Large Send Offload
Large Send Offload Slows Remote Desktop
I have issues with Hyper-V connectivity that appear to be resolved by disabling Large Send Offload IPv4 on the Virtual Machines.
The two problems this appears to resolve are Windows Updates not working and Remote Desktop being painfully slow.
The workaround until I found this setting was to change the VM to the legacy NIC
Windows Updates would not work on VMs although the machine quite happily browsed the web made the initial connection to windows updates and downloaded the latest window update client. Do not know if this is the case with WSUS.
The second issue I have just resolved is that Remote Desktop runs painfully slow although remote connections from the Hyper-V Manager are unaffected.